The modern amateur radio station is filled with software. It has been a long time indeed since this was a hardware hobby. Not only is there a lot of software, many of these applications communicate with each other and are connected to the public internet for our convenience and to access external services and to allow updates and maintenance.
Amateur radio software is no less susceptible to privacy and security flaws and risks other devices in our homes and pockets. Hams can be very trustworthy, however that trust comes with risks other than the assumed good intentions of the software authors. Danger lurks in the margins. What tweaked my current interest was an article about a backdoor in a popular SDR application.
This article is not specifically about that compromised software. I have nothing to say that isn't covered better elsewhere. This is an example of the software author, supposedly with good intentions, leaving a gaping security hole in its users' shacks. Exploiting the vulnerability is straight-forward, if you know that it's there. Some did know.
With that introduction let's look at a small sampling of the potential dangers of software. This is meant to make you wary and not to scare you away from ham software. I know hams that avoid all software they absolutely cannot live without. That's extreme and it's an attitude that will diminish your enjoyment of the hobby.
Signing authority
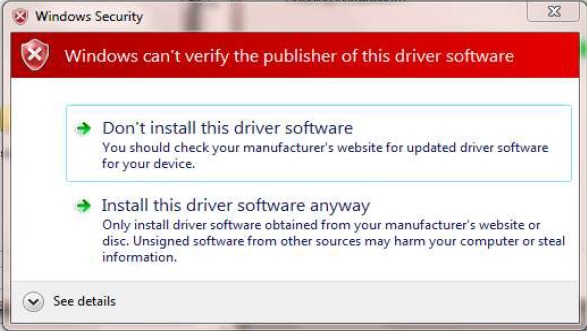
Signed software is safer than unsigned software. An application signed with a digital key issued by a reputable CA (certificate authority) provides a degree of assurance that the software came from the expected source. If in a subsequent download (e.g. update) the key is missing or different, or from a different CA, it should raise alarm bells. Don't install the software until you can verify that it is legitimate. In a minority of cases there may be a good reason for the change.
I have previously held the signing keys for two companies. They were closely guarded. An attacker that gains access to the keys can cloak malware as legitimate software. Losing the keys causing grief for the author and for the application's users. When you install digitally signed software you are trusting that the author has kept the keys secure.
I have a product that uses a root CA that is unrecognized by Windows. This is risky and Windows will understandably pester you about it. This CA issues the keys for the drivers used by the VNWA3 from SDR-Kits. I accepted the root CA and all is well. Users of products like this need to be diligent. Check user forums and other sources to validate as well as you can that it is safe before you proceed with installation.
Of course, quite a lot of ham and hobbyist software is unsigned. There is a cost involved to acquire and maintain the key, which hobbyist software authors may want to avoid. The CA is a business which has expenses and it must maintain high standards.
You can never easily know the trustworthiness of unsigned software. If it's open source you can inspect it for potential malware or flaws and then compile it yourself. However that is a tedious and difficult process that few of us would willingly undertake. It is easy to miss exploits, even by software professionals, since they can be disguised in many ways. You can hope that another user will spot the malware and make it public, yet the one mentioned earlier either went unremarked or unreported to the user base for years. Software updates must be similarly validated.
Desktop sharing
Desktop sharing apps have been around for a long time. Original uses included remote PC maintenance by IT personnel, and as a brute force means to share presentations and other live communications between individuals and groups. These applications are used for station remote control by allowing the station owner or another operator to use the station PC as if they were in the shack.
It should be obvious that protection of credentials is critical since if they are acquired by a bad actor (and it could be another ham!) the PC is compromised. After sharing credentials they should be revoked. New credentials can be created as required.
You probably want a free desktop sharing app, but don't be so cheap that you ignore who produces it and where it comes from. Commercial software is often more secure and that may be worth the price.
Phone apps
I have several radio related apps on my phone, and many hams have more. There are apps to monitor DX spotting networks, ham chat groups, radio remote control, and much more. The major apps stores -- Google and Apple -- are quite good at preventing malware from being distributed but cannot catch everything. For example, user privacy is often disrespected.
The app may ask for security permissions it does not require and the user may not be able or be interested in scrutinizing the app before installing it. Some of those permissions can be quite risky. But if you disagree you cannot use the app, and that will reduce the value of the associated hardware and software products: you are damned if you do and damned if you don't. Exploits can persist for a long time before being discovered. By then it could be too late.
It is safer to stick with reputable vendors but that is not a guarantee. Some risk taking is unavoidable. One thing to consider, particularly for Android, is to avoid side loading of apps. Side loaded apps are not scrutinized by the name brand app stores. The only apps I have side loaded are those I developed myself.
Don't click!
There are endless sites on the internet that promise free software and manuals for everything you can imagine, or that you can't imagine or wish you hadn't. Many of the popular search engines filter or flag suspect sites and those known to host malware. Not all do. Even the best may not have identified the latest rogue site.
In the pursuit of free too many people are tempted to click first and ask questions later. This is one of the highest risk things you can do on the internet. There are many zero-day exploits not yet patched by the browser and OS vendors, or your PC may not be up to date with patches for those vulnerabilities. Anti-virus software offers little protection against zero-day exploits. You must rely on your own good sense.
A single mouse click can ruin your day. There may be no recourse by the time you realize what has happened. Free can have an outrageously high price. It is better to pay for software and manuals. The companies and individuals deserve recompense. You will receive little sympathy for falling prey to the attackers that rely on your desire for a "good deal".
There's more...
This article touched on only a few potential security risks associated with ham software. There are too many for me to list, and I certainly couldn't make a complete list. The only difference with ham software compared is that the authors are usually individuals or small companies that may be unwilling or lack the expertise to keep their software secure.
My intent is to make you stop and think when you next download and use software for your station. Even software that comes from reputable manufacturers can pose risks since they may be cavalier about your privacy and security, or their internal security so lax that a third party or disgruntled employee can surreptitiously embed malware.
Consider this article food for thought. Think about risk the next time you download and install software onto your PC or phone, or update the firmware on your equipment. Guarantees are impossible but you can reduce the probability of becoming a victim by being sensible, careful and a responsible consumer of software and software products.